VMware introduced SAML login capabilities for the admin facing side of UAG with version 2106. See the following article: Release Notes for VMware Unified Access Gateway 2106
This quick home lab blog shows how easy it is and how to integrate this with VMware Workspace ONE Access as your entry point.
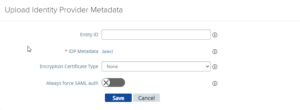
First things first, before we start you should have the IDP.xml file of your IDP in place if this is a VMware Access setup or Microsoft ADFS it doesn’t matter, the flow is exactly the same. You upload this at the identity bridging settings part of the UAG.
Then you go to the account settings part and select SAML Login Configuration and enable SAML authentication and select your IDP provider.
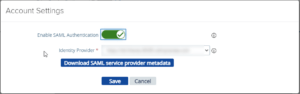
You click on Download SAML service provider metadata and select the identity provider and external hostname that resolves to the admin port of the UAG. (So yes a FQDN is needed and a valid certificate on the UAG admin facing NIC as well)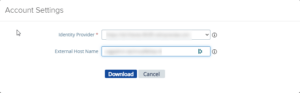
The saved XML file is used to import as a custom SAML2.0 web app in VMware Workspace ONE Access and there you can configure a custom access policy if needed.

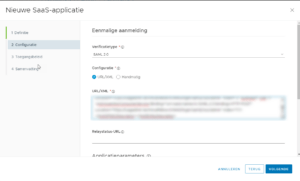
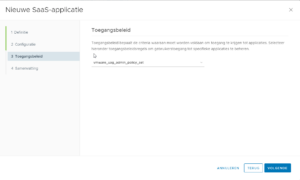
Afterwards when saving the configuration the admin interface will reset and afterwards only SAML login will work for the admin interface.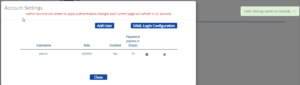
Some points to consider:
- There doesn’t seem to be a fallback login when SAML is configured
- When configuring the SAML part you might think you are stuck but simply after the SP.xml is downloaded click on cancel
- This setup should work for any other SAML IDP as well
- The user or group that is allowed to login via SAML is an ADMIN user
Hope it helps!