Just to start it off I’m assuming that the following is in place and fully configured and you are familiar with these concepts:
– XenMobile 10.x cluster (XMS)
– Active Directory (AD)
– Active Directory Certificate Services (ADCS)
– Active Directory Certificate Template(s)
– NetScaler Gateway (NSGW)
– Certificate Based Authentication (CBA)
Which all of them are combined in a XenMobile deployment which is configured to use CBA as an enrollment requirement.
I came across a limitation/by design issue in conjunction with the web enrollment of ADCS that XMS cannot solve, meaning that enrollment and requests for the first time will work just fine but when you revoke or selective wipe a device/user and the latter enrolls again you will get a cached certificate from XMS (you say what…) Revocation in XMS will work just fine but not at this point because according to support the API used in ADCS is not capable of doing a revocation, and basically XMS is using the web-enrollment for this and relying on that.
If you want to check it just enroll a user with the above setup and check for yourself, user gets revoked, you revoke the user certificate in ADCS and enroll again and you will see the cached certificate being issued from XMS (and no new issued certificate from ADCS)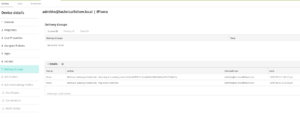
But there is a workaround/solution for this, query the XMS database for this certificate and select the user certificate to delete..
The following query will give you the certificates which are present on XMS
Select * from dbo.keystore where name like ‘%ag%’
To delete the certificate you execute this query with your ID (in my case 22)
Delete from dbo.keystore where id=22
After this the cached gateway certificate is deleted and with a new enrollment you will also get a new certificate.
UPDATE:
When combining the above with a CRL or OCSP integration on the NetScaler this will give an automatic renewal request for the device, meaning no manual action needed anymore. This seems to be a builtin behaviour client side (Secure Hub) see the following article for more information: https://docs.citrix.com/en-us/netscaler/11-1/ssl/manage-cert-revocate-lists.html