I like to fiddle around with possibilities when it comes to SAML, OAUTH authentications. This all started when a customer engineer triggered me with the possibility of achieving an SSO experience with the Citrix NetScaler and using VMware Access as the source of truth for authentication.
Well guess what this works! And even for the native workspace app users as well. All with the conditional access policies of VMware Access before it.
First things first, I’m expecting that you know how to use the following and already have that in place:
- Configured Citrix CVAD with Citrix Gateway doesn’t matter if it is Unified or not
- Advanced authentication profile for SAML usage in Citrix Gateway
- AAA setup to be used with the SAML / authentication profile
- Working Citrix session policies set for web and native logins
- VMware Access (Workspace ONE) on-premises or cloud variant
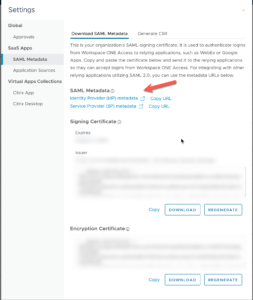
To start this sort of configuration, first you will need to download the VMware Access IdP SAML metadata or copy the URL of it and paste this in Citrix NetScaler:
The important part is that if you do not allow the NetScaler to have outgoing internet access it cannot validate the SAML metadata discovery, and everything will fail. In this case upload the IdP metadata as a certificate on the NetScaler and deselect the “Import Metadata” option the SAML Server action. Either way make sure that this is working for you.
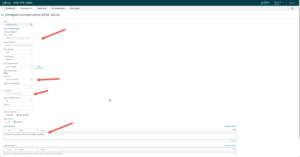
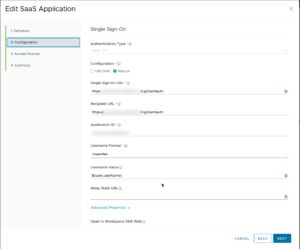
Regarding the SAML Server action the “${user.userName}” value is the unique object in VMware Access which translates to either sAMAccountName or userPrincipalName according to your setup. With this value it will always work as expected with the logon.
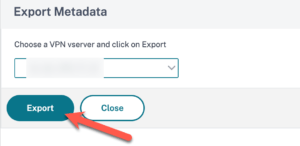
When all the values are correct you can export the SAML metadata to be used in VMware Access as a new SaaS SAML 2.0 application. Paste the XML input in this app and assign the application to your test user/group. Make sure the application id and issuer name align between VMware Access and Citrix NetScaler.
To summarize above and a working setup:
- Authentication Profile is mandatory otherwise you are not working with advanced authentication on Citrix Gateway
- Citrix Gateway combines with a AAA for this feature
- Make sure the URL’s match at both sides otherwise it will fail
- Don’t forget the Relay State Rule in NetScaler for SAML security
Hope it helps! And if there are any questions give me a ping.