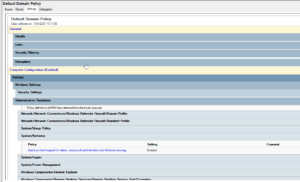
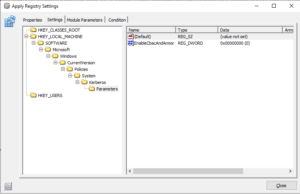
On my current customer project we’ve encountered a strange issue when some stricter security policies were implemented. Kerberos armoring was enabled which effectively broke the instant clone process for Windows 10 1809/1909 releases but not for 2009 or 21H2.
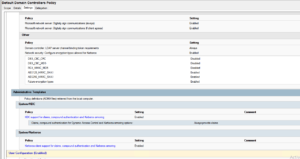
It all started with a ticket that the image update process in Horizon would error out and fail constantly on the mentioned images. On the newer builds no problem at all. At first we thought it was an Microsoft update of some sorts but after some troubleshooting with colleagues Wesley Kieffer and JP Ruitenbeek it turned out to be new hardening items which got turned on.
When clearing the before setting in the image and then sealing the older images would update just fine. After reproducing the entire setup in my own lab I encountered the same issue as well. Opened up a VMware support case which still is being worked at.
The setup being used is VMware Horizon 7.13.1
The following article also describes how you can troubleshoot the internal VM which is being used for the cloning process: Troubleshooting Instant Clones in the Internal VM Debug Mode
And for some more information regarding Kerberos armoring see What’s New in Kerberos Authentication | Microsoft Docs and Compound Authentication and Active Directory Domain Services claims in Active Directory Federation Services | Microsoft Docs
Hope it helps!
UPDATE:
After a long wait from VMware support and pitching in some R&D time this resulted in an it’s going to be a feature update. Currently VMware Horizon code base isn’t aware of Kerberos armoring. It’s not just version 7.x but also 8.x which is affected. The workaround above is the solution until instant clone technology will get an update in the nearby future. This could take up to about six months. I’ll post back the update when it’s final.